BLOG
Research
New Vulnerability Allows for Next Generation Rogue Access Point
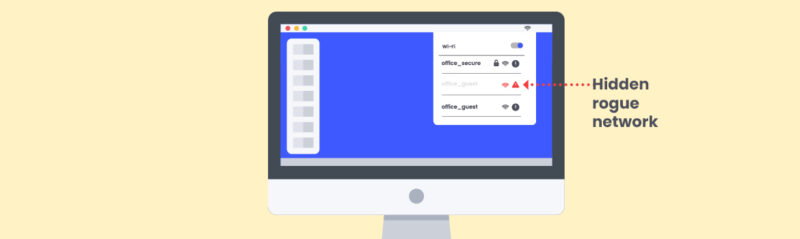
By Uriya Elkayam - As part of our research, we found a vulnerability by-design in the Wi-Fi protocol that under OWE mode exposes Hidden Networks. This means that a hidden wireless network name is open to all, not just to a device attempting to access a pre-known hidden network.
Feb