Home | Technology | Platform | How it Works
Secure Your Network Airspace with Aireye
Continuous monitoring and policy enforcement for your organization’s wireless security.
AI-driven, Saas, Zero-touch, Non-intrusive
Aireye is the only platform that delivers complete network airspace situational awareness. It continuously monitors all active communications, identifies authorized and unauthorized transmissions, detects communication control lapses, and pinpoints unauthorized devices in real-time. Automatically enforce your wireless security policy and prevent wireless attacks with Aireye’s out-of-the-box solution.

Identify
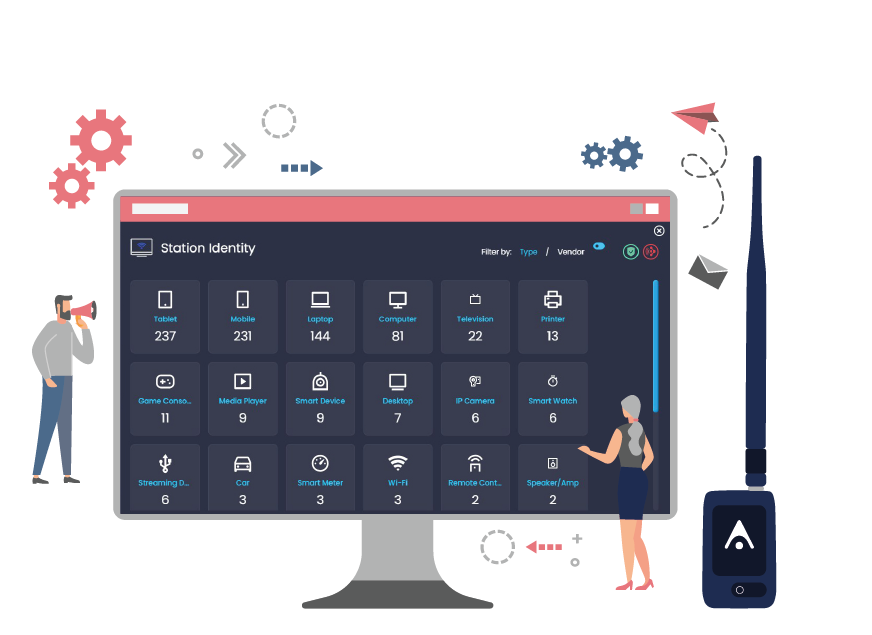
Identify the different entities mapped in the airspace. Classify the entities and their interactions.
In particular, the AirEye Dome differentiates between corporate networks and stations, aka Wireless Receptors, and networks generated by non-corporate assets and non-corporate stations, aka Antenna for Hire.
AirEye Dome further adds additional attributes and characteristics to the different entities based on technical aspects of their communication and their behavior.
AirEye does this by employing protocol analysis tools as well as Machine Learning algorithms.

Visualize
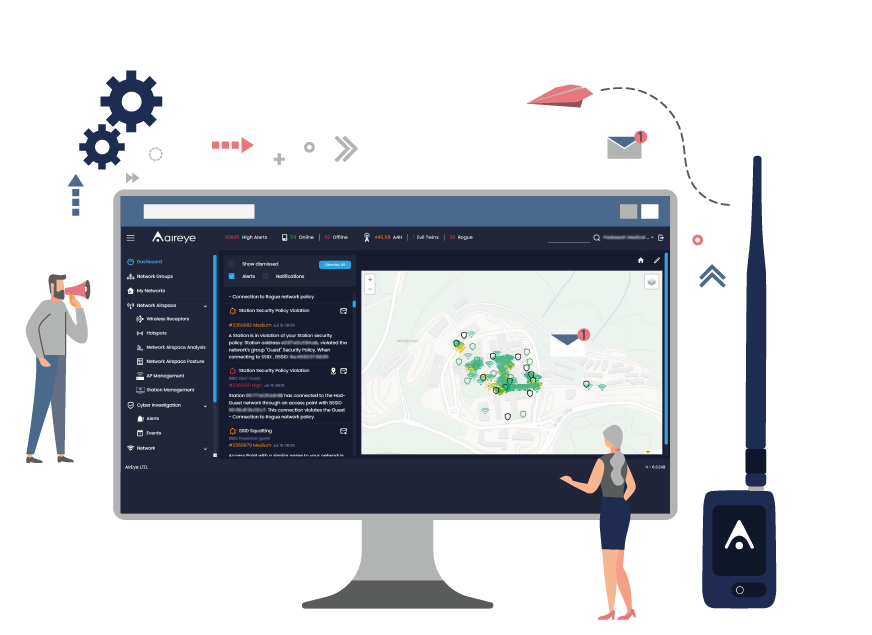
Continuously monitor and analyze all wireless communication channels broadcasting in your corporate airspace in real time.
AirEye Dome maps all entities within the network airspace over time. These include Access Points (APs), stations, hotspots, Peer-to- Peer services, and others. AirEye Dome also maps the interactions between these entities.
In parallel to AirEye’s monitoring technology which creates a persistent map of all entities and their interactions, AirEye provides real-time continuous monitoring of such interactions.
Together, the ongoing mapping with the real-time tracking, feed the identification and detection mechanisms of the AirEye Dome.
Control
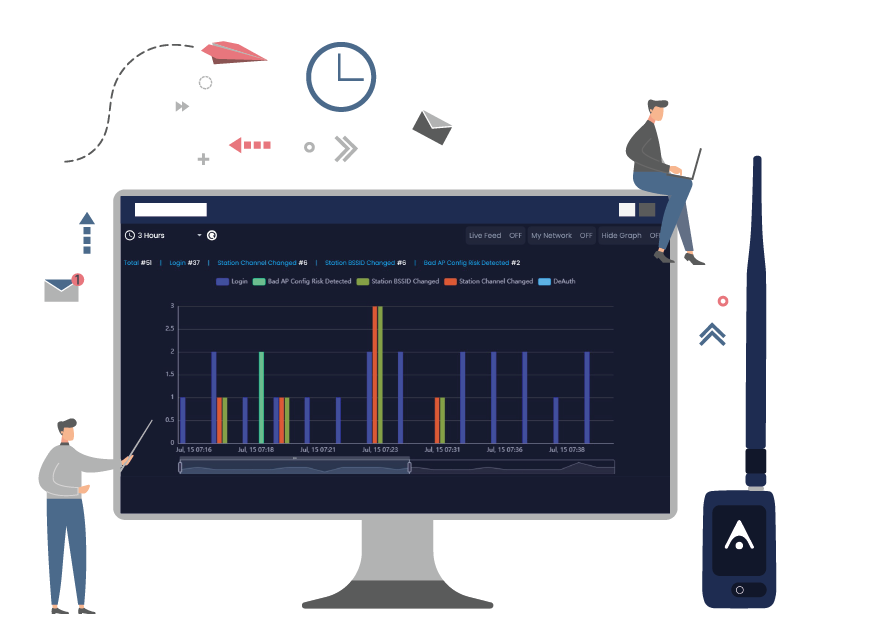
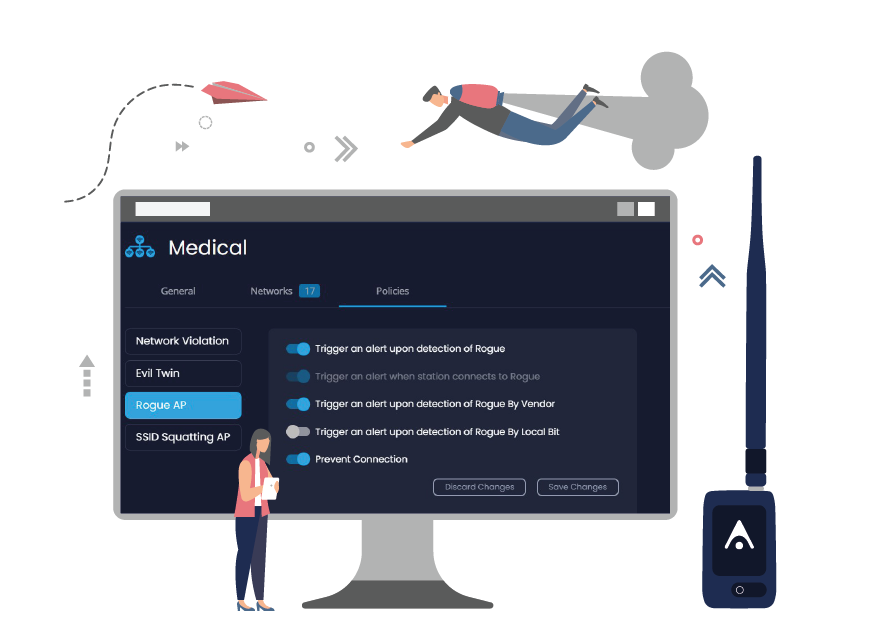
Enforce a corporate wireless security policy over the network airspace by identifying threats and detecting unauthorized interactions.
AirEye Dome issues an alert when a threat to corporate assets is identified per a corporate policy. These include rogue APs, Evil Twin, hotspots on corporate networks and more. All of which may result in unauthorized network access, device hijacking, segmentation hopping or data leakage.
The AirEye Dome detects and alerts in real-time when an interaction between a non-corporate device and a corporate entity is either part of a wireless attack or in violation of corporate wireless security policy. Such interactions may include corporate workstations connecting to external hotspots, sensitive devices connecting to Guest networks, or external stations communicating with corporate Peer-to-Peer services.

Prevent
Automatically terminate any violating interactions between entities involved.
When the AirEye Dome identifies a violating interaction attempt, it stops that single precise interaction. All other communications continue as usual.
Only the violating connection is terminated. AirEye does not jam networks, nor is there any impact to any other networks.
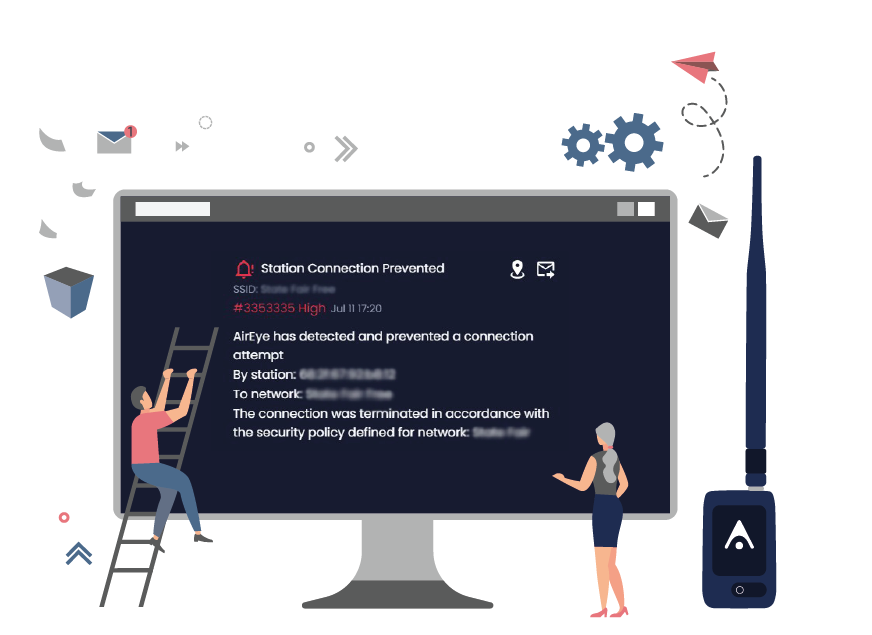

Forensics
The AirEye Dome provides multiple built-in reports for executives and operations managers on blocked wireless attacks and prevented policy violations.
Attack-related reports provide the full attack story, including when the attack happened, what happened, how it happened and devices involved.
Violation-related reports include company wireless security policy violations as well as adherence to wireless-related aspects of industry standards and regulations such as PCI-DSS.

Simple Setup
Our platform does not need integration with existing systems like switches, APs, firewall or any other to be effective.