Home | About | Blog
Blog

Does Micro-Segmentation Really Offer Ultimate Protection for OT/IoT/IoMT Devices?
aireye
Micro-segmentation – dividing up your network and setting controls for each part – is currently the trendy solution to have for securing OT, IoT, and IoMT devices, but this belief overlooks several critical realities. Limited Visibility Problem: In environments with OT, IoT, and IoMT devices, installing agents is not feasible,
Subscribe to Our Newsletter

New Vulnerability Allows for Next Generation Rogue Access Point
February 23, 2023
Network Security Listing
November 30, 2022


The Network Security Stack
November 14, 2022
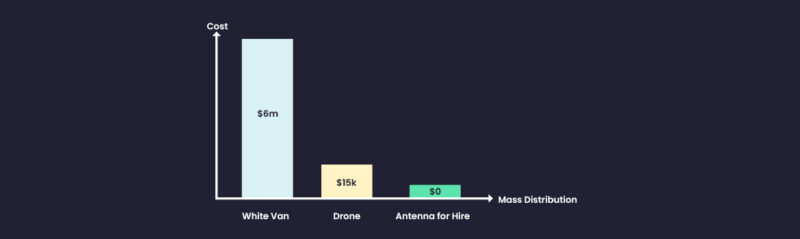
Wi-Fi Attacks: From White Vans, to Drones and on to Antenna for Hire
October 13, 2022
First-hand Account of an Anatomy of a Wireless Attack/ Hedgehog Security
September 1, 2022


AirDrop: The Hackers Tool for Dummies
May 11, 2022

Wi-Fi Spoofing: Employing RLO to SSID Stripping
April 4, 2022
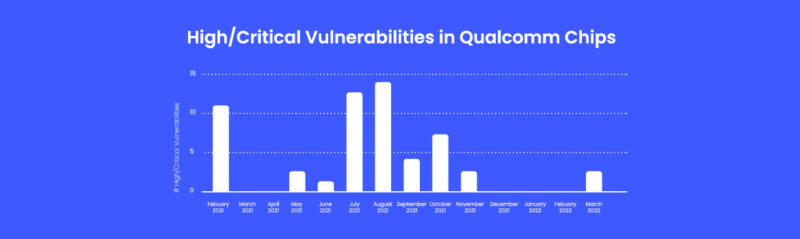
Trends in Wi-Fi Vulnerabilities: This Time, It’s Qualcomm
March 29, 2022




The NACP Monthly News Roundup – November 2021
November 30, 2021

AirEye Appoints Jason Lish to Advisory Board
November 11, 2021

The NACP Monthly News Roundup – October 2021
October 31, 2021

The SSID Stripping Vulnerability: When You Don’t See What You Get
September 13, 2021

The problem with NSA’s public wireless guidance
August 2, 2021

New Survey Reveals Hackers’ Best-Kept Secret
July 1, 2021


Amazon Sidewalk: The Enterprise Wireless Security Angle
June 17, 2021



AirEye secures the invisible Corporate Network Airspace
October 19, 2020



Network Security Listing
November 30, 2022

The Network Security Stack
November 14, 2022

The problem with NSA’s public wireless guidance
August 2, 2021

Wi-Fi Attacks: From White Vans, to Drones and on to Antenna for Hire
October 13, 2022

AirDrop: The Hackers Tool for Dummies
May 11, 2022


First-hand Account of an Anatomy of a Wireless Attack/ Hedgehog Security
September 1, 2022

New Vulnerability Allows for Next Generation Rogue Access Point
February 23, 2023

Wi-Fi Spoofing: Employing RLO to SSID Stripping
April 4, 2022

Trends in Wi-Fi Vulnerabilities: This Time, It’s Qualcomm
March 29, 2022


The NACP Monthly News Roundup – November 2021
November 30, 2021

The NACP Monthly News Roundup – October 2021
October 31, 2021

The SSID Stripping Vulnerability: When You Don’t See What You Get
September 13, 2021

New Survey Reveals Hackers’ Best-Kept Secret
July 1, 2021



Amazon Sidewalk: The Enterprise Wireless Security Angle
June 17, 2021



AirEye secures the invisible Corporate Network Airspace
October 19, 2020
