The Air is Hostile Territory: Why Cybersecurity Without Wireless Detection and Response is Only Half a Strategy
Your perimeter is protected. Your endpoints are monitored. Your network is segmented.And yet — attackers are bypassing all of it. Through the network airspace. Most security strategies still assume wireless threats are limited by proximity. That’s outdated.With off-the-shelf tools and Antenna-for-Hire services, attackers can now reach your environment without stepping foot near it — dramatically […]
Rogue Access Points Are Back — And Smarter Than Ever
They were one of the first wireless threats ever documented. Simple, crude, and often misconfigured — rogue access points used to be the rookie mistake of the early 2000s. But today? They’re back. And they’ve evolved. What was once the domain of interns plugging in Wi-Fi routers “for convenience” is now the playground of red […]
Threat Modeling the Wireless Airspace in 2025

“Any Wi-Fi Attack Can Now Be a Remote Attack” By the AirEye Research TeamInspired by Mathy Vanhoef’s insights 1. Objective Wireless threats are no longer bound to physical proximity. Pre-auth vulnerabilities, beacon spoofing, and rogue access points can now be exploited remotely — even globally — thanks to cloud relays, malicious proxies, and antenna-for-hire models. […]
New Survey Reveals Hackers’ Best-Kept Secret

Do attackers leverage the corporate network airspace to conduct their nefarious activities such as gaining unauthorized access to the…
The Apple format string bug: From a silly prank to an airborne attack

At AirEye we analyze, research and learn Wi-Fi related attacks. What we found was that although the latest iPhone Format String flaw is…
Amazon Sidewalk: The Enterprise Wireless Security Angle

Last week Amazon released Sidewalk – a low-bandwidth network between Sidewalk Bridge devices. While Sidewalk is grabbing consumer…
FragAttacks + Antenna for Hire: The Perfect Storm in Your Network Airspace
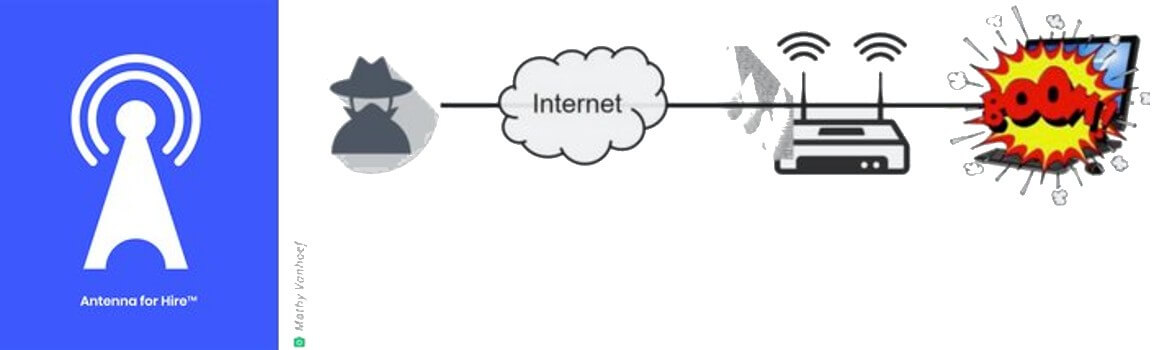
Coupling FragAttacks with Antenna for Hire means that the attacks can be carried out remotely
AirEye Raises $8M Series A to Extend Network Security into the Unprotected Digital Airspace

AirEye is the first solution to block attacks against corporations launched from Antenna for Hire devices in the network airspace
AirEye secures the invisible Corporate Network Airspace

Ohad Plotnik, Aorato’s co-founder, serial entrepreneur and Finjan founder Shlomo Touboul, and Amichai Schulman, Imperva’s co-founder,…
