Why You Should Look at Your Corporate Network Airspace
The majority of the corporate devices today include dual connectivity – on one hand connected to the corporate network and on the the other, acting as Wireless Receptors open to connecting to any wireless channel.
The vicinity of the corporate is also about with Antenna for Hire – broadcasting wireless devices.
While it is the corporate wireless security policy to allow employees and corporate-controlled devices to communicate only on supervised channels, corporations find that they cannot effectively enforce that wireless policy.
For example, a common policy violation occurs when an employee that is required to communicate over a restricted wireless network turns to a less restricted, or even a Guest or an open network when lacking wireless reception.
Attackers are also aware of this lack of control and enforcement and leverage Antenna for Hire as a proxy to penetrate the corporate network through Wireless Receptors.

In fact, an AirEye survey showed that 44% of experienced IR professionals investigated incidents related to wireless attacks or vulnerabilities.
40% of surveyors mentioned they did not have sufficient forensic data in such attacks, and another 40% were not sure whether data was leaked. By not leaving forensics or attack data, this attack surface is used over and over again by attackers.
Who Should Care About Their Network Airspace?
Each company needs to consider their network airspace security as part of their network security strategy.
The endless number of wireless broadcasting devices in the vicinity of the network means that each company today needs to have visibility into all their corporate networks – including shadow networks, have a solid wireless security policy that is enforceable and be capable of preventing wireless attacks.
These include financial companies, banks, telcos, manufacturing, healthcare, retailers, software companies and defense.
Companies must enforce their wireless security policy and protect their corporate network airspace to eliminate the risk of:
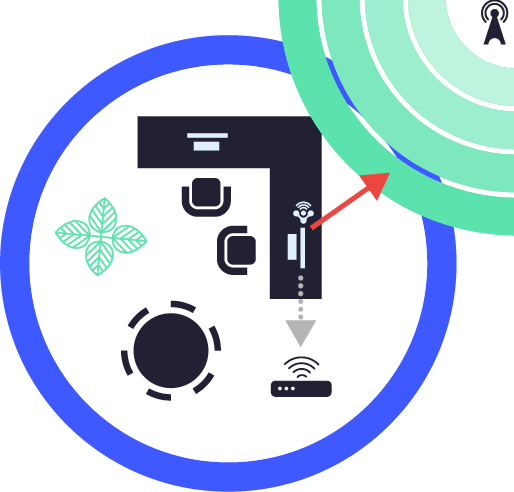
Unauthorized access to the corporate network

Device hijacking
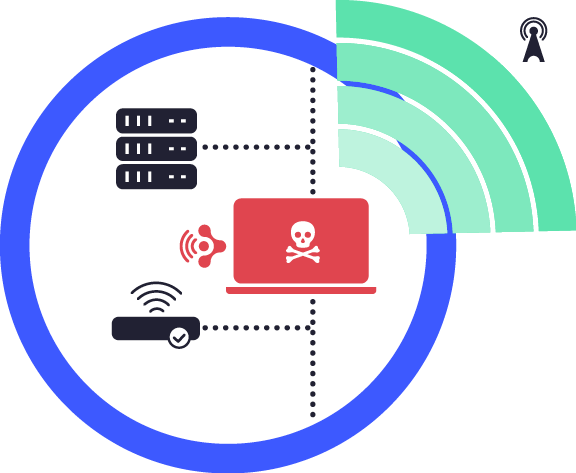
Data Leakage
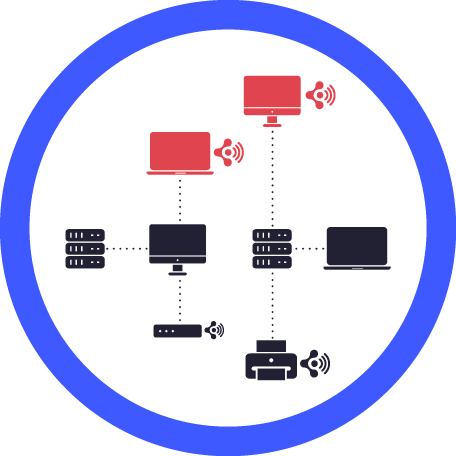
Segmentation hopping
How Medical Devices Can Be Easily Exploited (And Protected)

A4H Reconnaissance

A4H Control
WR Reconnaissance
Exploit

Unauthorized Network Access

Segmentation Hopping

C&C Communications & Exfiltration
Wireless Attacks Are Remote and Software Based
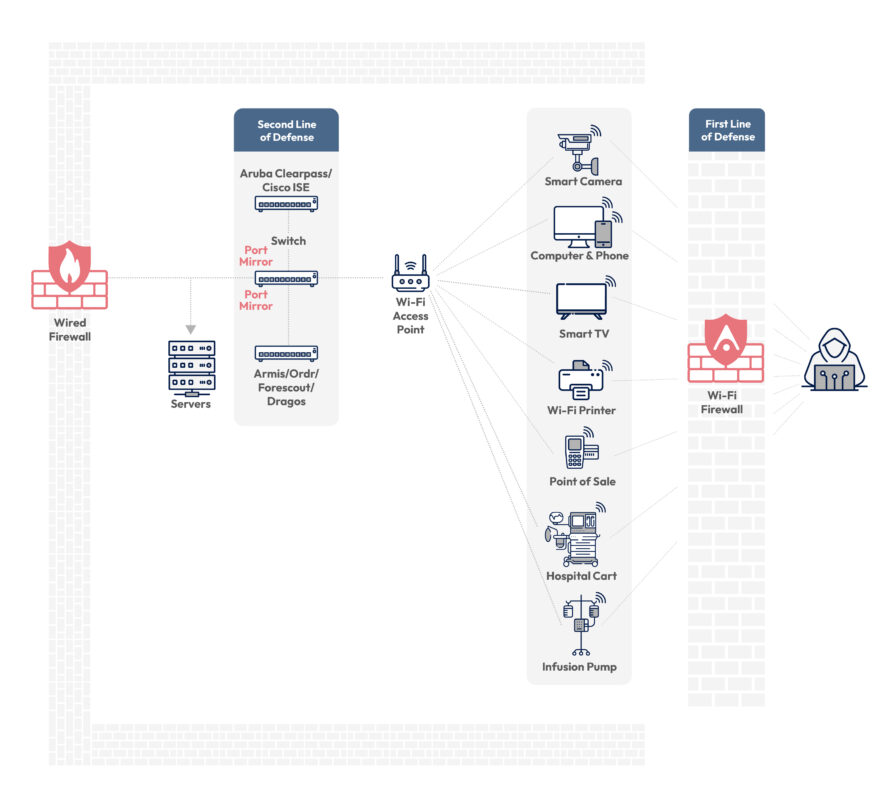
The corporate IT landscape includes an increasing number of Wireless Receptors – wireless-capable devices, ranging from corporate laptops, printers, and even coffee machines. Each of these may create shadow networks, flying under the radar of the security team, and posing a security risk to the corporate network.
Outside the corporate, there is an endless number of Antenna for Hire – wireless devices broadcasting in the vicinity of the organization, ranging from security cameras to a router at a nearby cafe.
Attackers leverage the Antenna for Hire and gain unauthorized network access, device hijacking or data leakage, using Wireless Receptors as a springboard into the corporate network.
In essence, the Antenna for Hire acts as a proxy for the attacker without needing to physically be in the vicinity of the corporate.
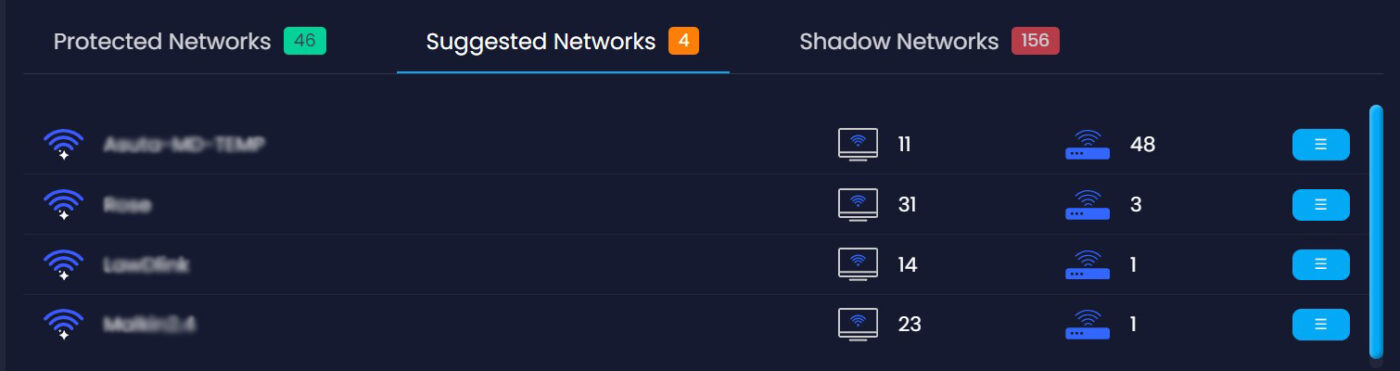
Shadow Networks
One of the biggest concerns security teams is shadow networks – networks generated by corporate-controlled devices.
No security solution today apart from NACP can identify, monitor and place controls over shadow networks.
Here are just a few examples of network entry points that are created by shadow networks and the risk they pose:

Entry Point

Security Risk





