At AirEye we analyze, research and learn Wi-Fi related attacks. What we found was that although the latest iPhone Format String flaw is perceived as seemingly benign, the implications of this vulnerability stretch far and beyond any joking matter. If you are responsible for the security of your organization, you should be aware of this vulnerability as a related attack can affect corporate data while bypassing common security controls such as NAC, firewalls and DLP solutions.
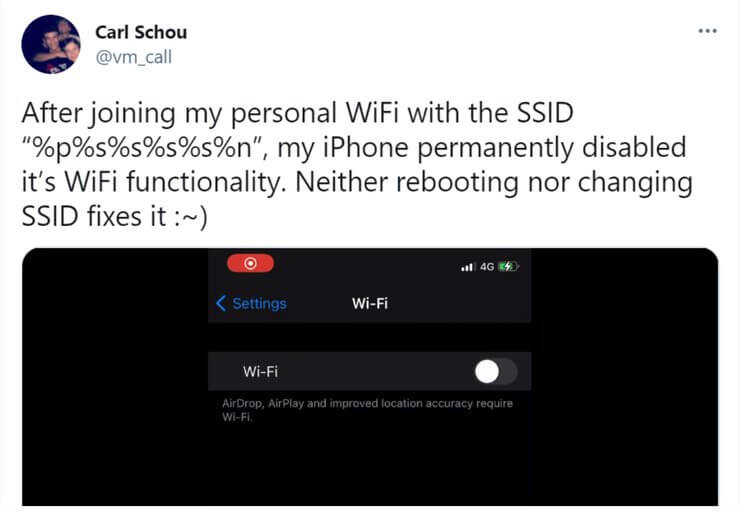
To recap, over the weekend, security researcher Carl Shou disclosed an iPhone format string flaw which allows any attacker to disable an iPhone’s Wi-Fi capability. This flaw received light-hearted attention, looking at it mainly through the lens of pranksters.
Taken from: https://twitter.com/vm_call/status/1405937492642123782
The vulnerability stems from a piece of code that writes log entries after making an attempt to connect to a wireless network.
As part of AirEye’s ongoing research into the network airspace – all wireless channels in the vicinity of the corporate – we further analyzed this vulnerability to understand its ramifications and have found that:
- The vulnerability is not restricted to the iOS operating system. In particular it also affects the MacOS operating system used by many corporations for employee stations, including MacBook Pro.
- An attack may lead to remote code execution. While it is easy to use the vulnerability to simply disable the Wi-Fi capabilities of an attacked machine, the nature of format string vulnerabilities is that when carefully crafted they can be used to write arbitrary code into random, or chosen, parts of a machine’s memory – and even eventually inject and execute code. Since the device is on the corporate network, this code can eventually be used for lateral movement.
- An attack exploiting the flaw does not require physical presence. A remote attacker can exploit Antenna for Hire in the proximity of the corporation to quickly turn it into an attack tool against all Apple devices in the corporate network. An Antenna for Hire can be any wireless-enabled device, outside of the corporation control, such as a security camera over the street, an AP of a nearby coffee shop, personal mobile phones of guests and even laptops of employees in neighboring offices. From our experience in the field, we have found that there are 30K potential Antenna for Hire in the proximity of a typical organization.
- Firewalls, NACs and Secure WLANs do not address this type of attack. The attack traffic is **not** part of the corporate network and hence any traditional network security solution remains completely oblivious to it. In fact, attack traffic can be sent over channels that are not used for corporate network traffic. Consequently, the attack goes undetected by network security solutions and does not leave any trace in the forensics and networking logs.
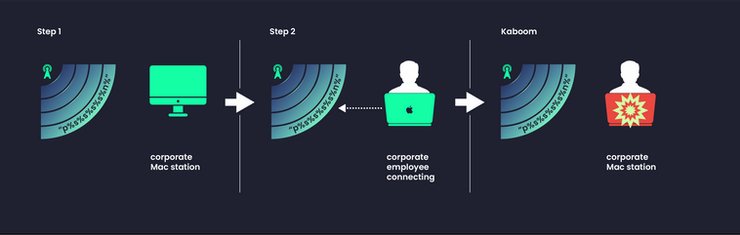
The network airspace: the new attack surface
This Apple format flaw is yet another example of a digital airborne attack which leverages the corporate network airspace, bypassing security controls and leaving no trace in the network logs.
In the past few months we have seen a slew of published digital airborne attacks – the AWDL attack, FragAttacks and this one. These three incidents are drawing a clear trend line of this new attack surface. The AWDL vulnerability was a sophisticated attack against a proprietary Apple protocol; the FragAttacks target a less common feature of the general wireless protocol which may explain why the remained undetected for many years; the new Apple format string vulnerability shows that even the most fundamental message exchange over the wireless medium (i.e. network recognition) may still be vulnerable. Now that researchers are starting to dig into Wi-Fi protocols, we should expect more such vulnerabilities, across all operating systems, to surface.
The corporate network airspace is rapidly becoming the go-to-place for attackers. Airborne attacks are new and as-yet an unaddressed threat vector. Given their stealthy nature we’re bound to see more such attacks.
What can enterprises do?
Since a digital airborne attack operates on the network airspace dimension, the only way to effectively and efficiently thwart such attacks is by protecting the network airspace.
A Network Airspace Control and Protection (NACP) solution continuously monitors all channels in the corporate proximity as well as all devices and assets. Accordingly, it detects any security or wireless policy violation, such as communications that carry this latest attack vector. The NACP solution can then take an appropriate action to mitigate the threat or remedy the policy violation, while providing the full details to construct the attack story.
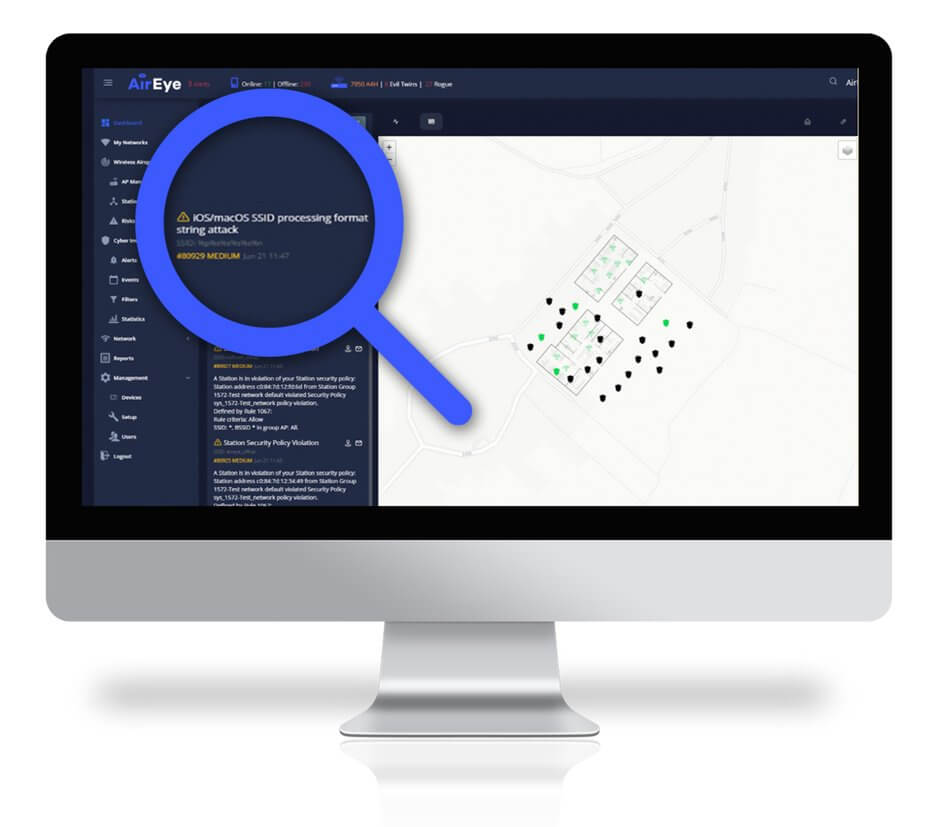
AirEye vs Apple String Format Flaw
AirEye Dome, the leading NACP solution, detects an attack leveraging the Apple Format String flaw and automatically quarantines the device from the corporate network.