New Survey Reveals Hackers’ Best-Kept Secret

Do attackers leverage the corporate network airspace to conduct their nefarious activities such as gaining unauthorized access to the…
FragAttacks + Antenna for Hire: The Perfect Storm in Your Network Airspace
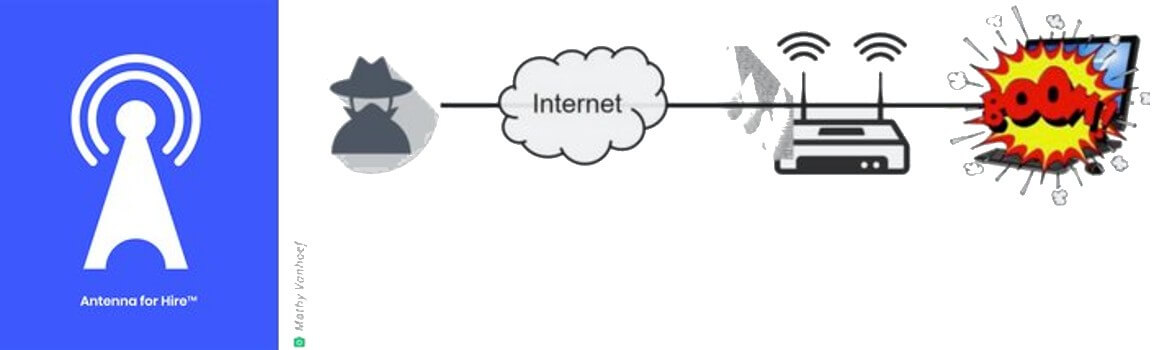
Coupling FragAttacks with Antenna for Hire means that the attacks can be carried out remotely
AirEye secures the invisible Corporate Network Airspace

Ohad Plotnik, Aorato’s co-founder, serial entrepreneur and Finjan founder Shlomo Touboul, and Amichai Schulman, Imperva’s co-founder,…
