Control Your Network Airspace
From preventing connections between corporate devices and unauthorized wireless networks to ensuring that devices are not communicating on unmonitored networks, Aireye automatically enforces your wireless security policy.

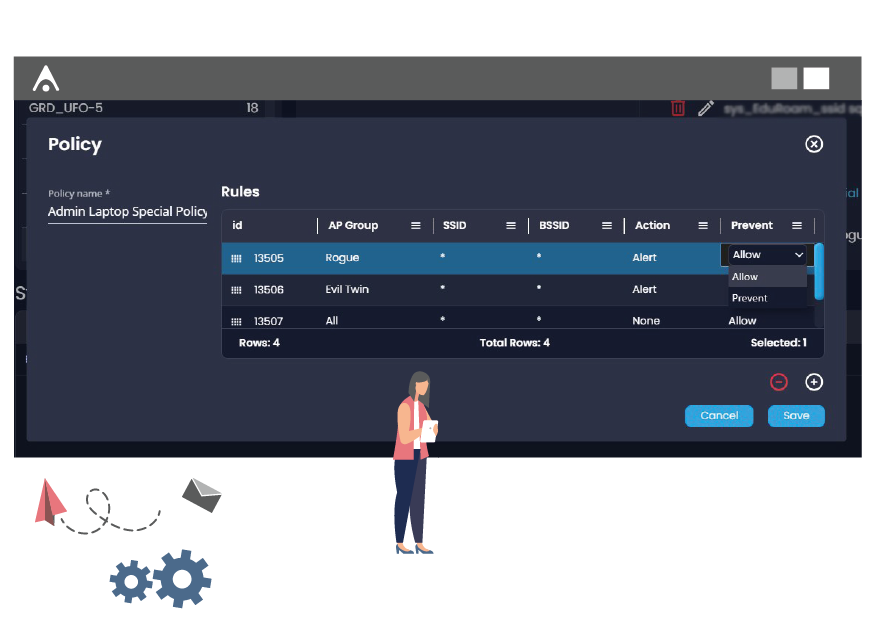
Easily define your wireless security policy
Your wireless security policy should be clear: no corporate device should connect to an unauthorized or unmonitored network. With AirEye implementing that policy is easy.
The AirEye platform allows you to easily build and customize your wireless security policy to your environment based on the networks that AirEye continuously discovers such as shadow networks, guest networks, peer-to-peer networks, and hotspots.
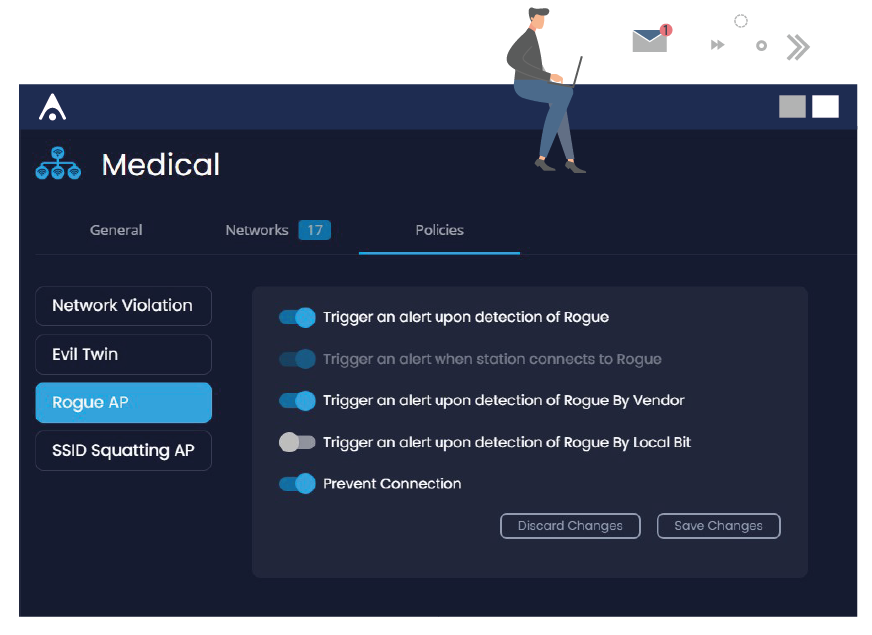
Add the exceptions that you need
Forget trying workarounds, bypasses and vendorchasing to add exceptions and contingencies to your policy. Do you need a wireless printer so that the graphic designer can print from their iPad? Does your lab need an external Internet connection?
AirEye enables you to easily add exceptions relevant to your business, such as allowing certain communications from certain devices or allowing particular wireless networks for periods of time.
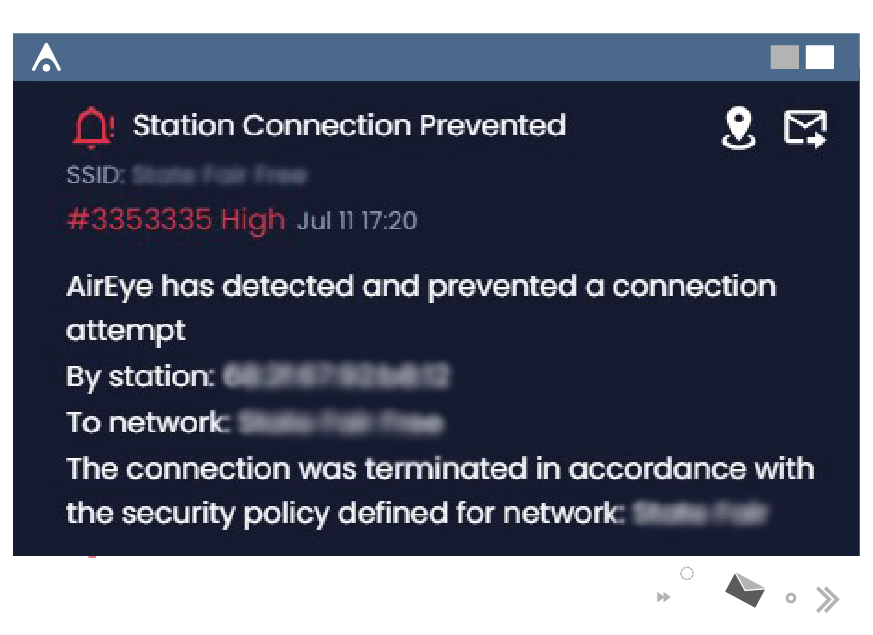
Prevent wireless security policy violations
AirEye enables you to gain control over your network airspace by continuously monitoring your network airspace against your wireless security policy.
Any violating connection attempt is automatically and immediately prevented by AirEye.
Feed your SIEM with network airspace related alerts and violations
Integrate with your chosen SIEM or SOC tool through AirEye’s Rest API.