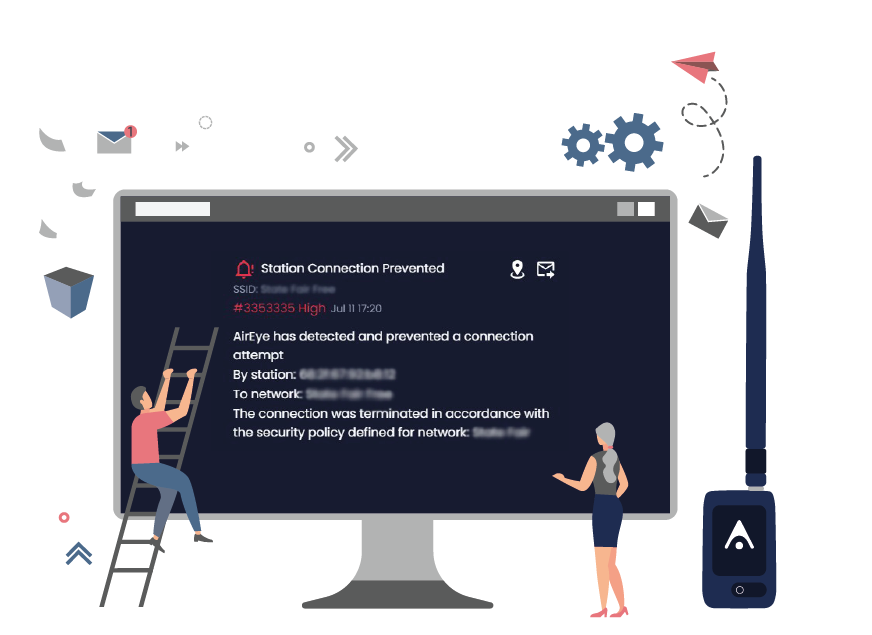
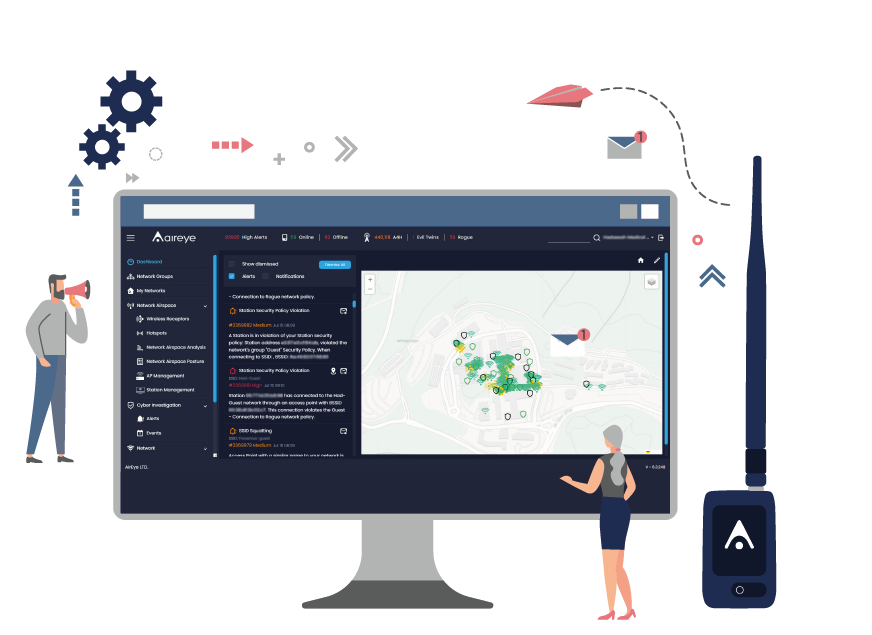
Pioneering Wireless Security and Protecting Your Critical Assets
Aireye is the first WDR (Wireless Detection and Response) platform. It delivers cutting-edge security for all IT and OT assets, individually protecting each Wi-Fi-enabled asset without isolating them from the network.
Agentless | AI-driven | SaaS | Zero-Trust | Turnkey

Pioneering Wireless Security and Protecting Your Critical Assets
Agentless | AI-driven | SaaS | Zero-Trust | Turnkey
Pioneering Wireless Security and Protecting Your Critical Assets
Agentless | AI-driven | SaaS | Zero-Trust | Turnkey

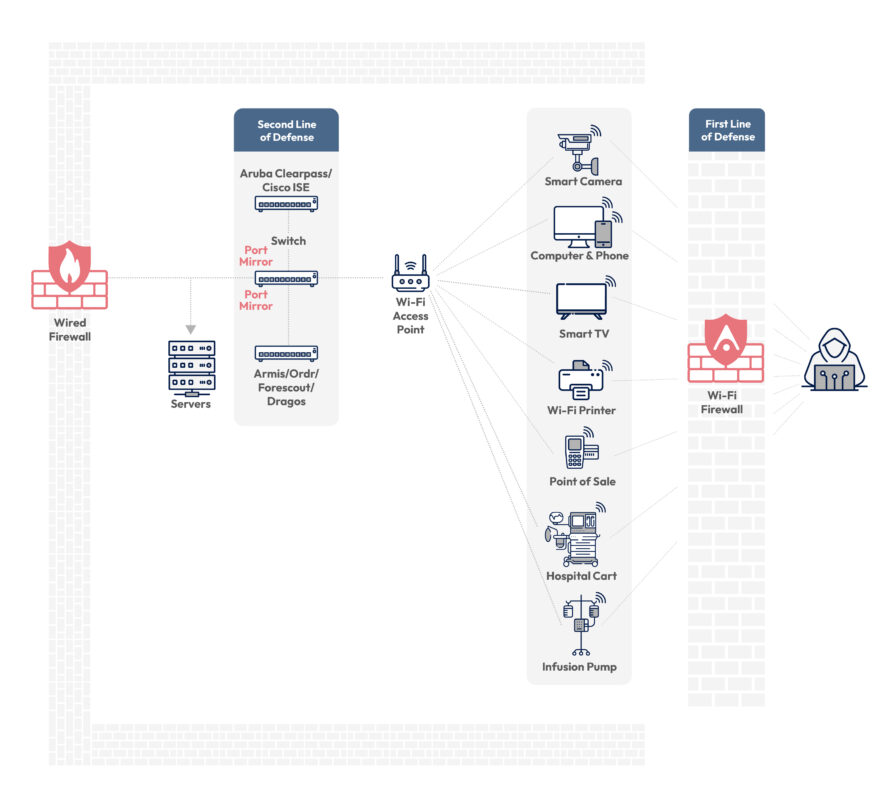
The Ever-Growing Attack Surface
Rapid growth of Wi-Fi presents critical challenges and threats:

Rapid growth of Wi-Fi assets: 12 billion Wi-Fi assets today, projected to exceed 30 billion by 2030

Increased exploitability: There are nearly 2,000 Wi-Fi CVEs currently, expected to grow to over 10,000 by 2030

Proximity of threats not limited to Wi-Fi signal range: Search engines like Shodan make it trivial to locate vulnerable Wi-Fi devices near customer buildings. Small businesses often lack rigorous security measures, making their Wi-Fi devices potential entry points for attackers, including rogue nations, posing significant security threats to customers, who have no control over these exploitable assets
Finally – something you can do, today! Protect your critical assets and prevent the next breach caused by a blind spot, with Aireye.
Finally – something you can do today
Protect your critical assets and prevent the next breach caused by a blind spot

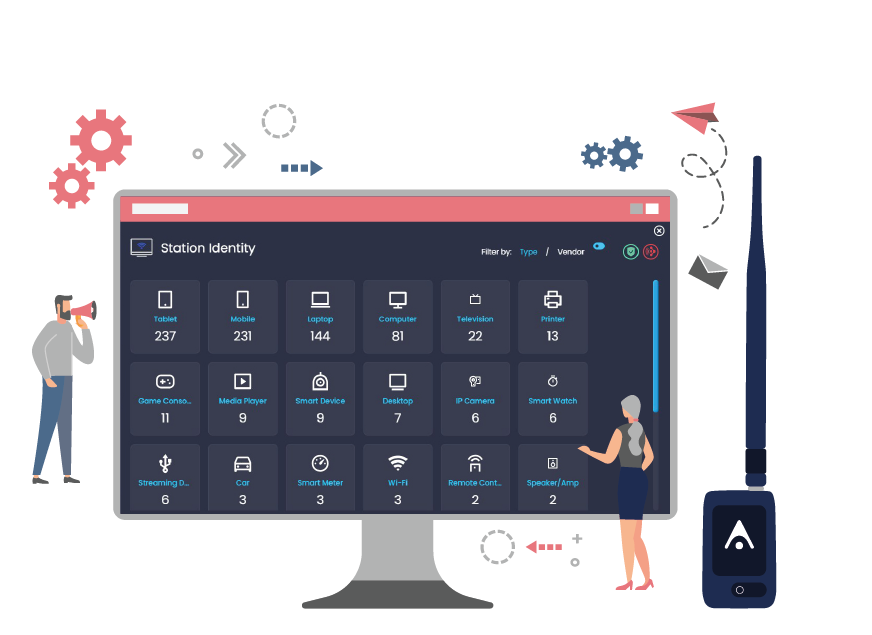
Identify & Classify

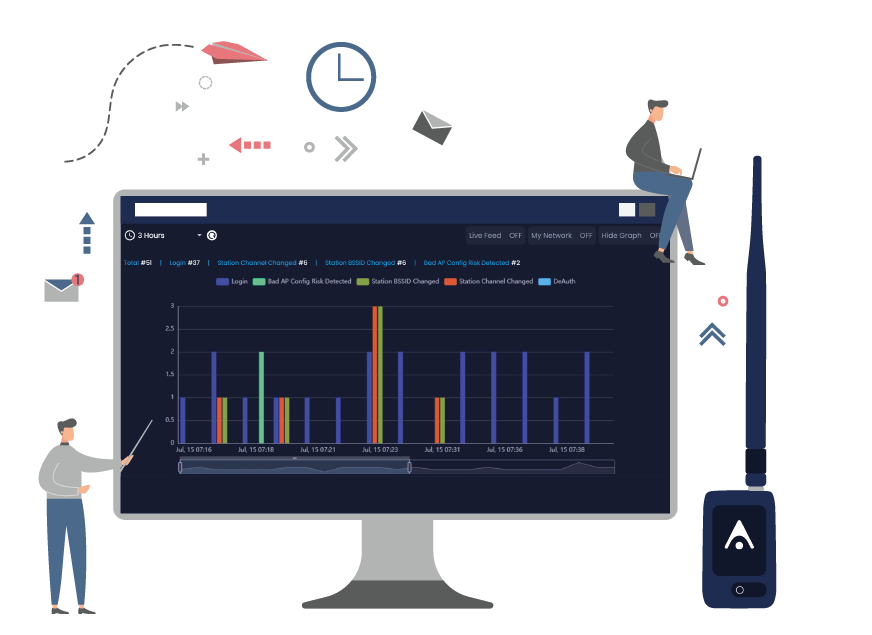
Visualize

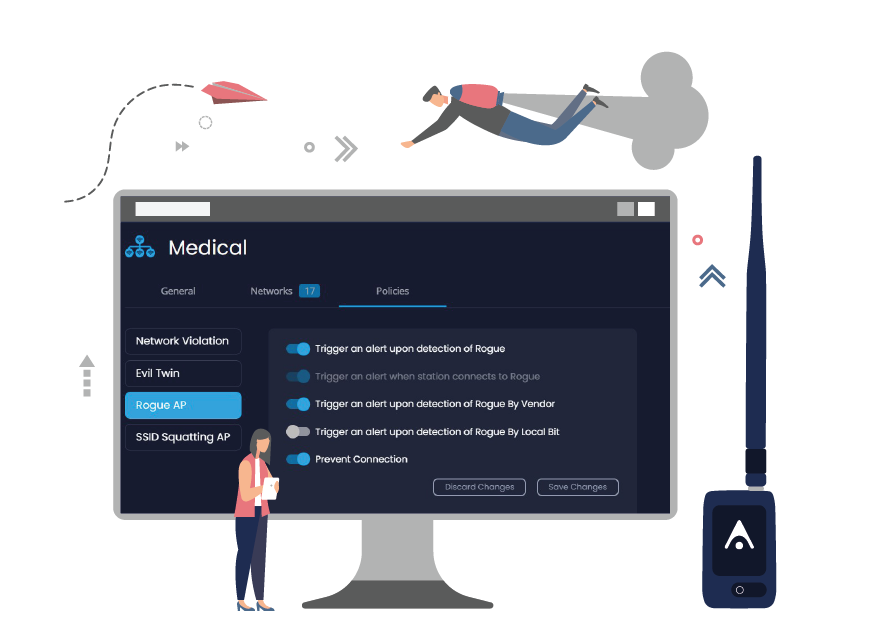
Control
 Aireye’s SaaS solution requires no network or architectural changes...
Medical devices are life-critical - Aireye ensures no unauthorized connections to Hadassah’s devices and prevents…. this was just a policy on paper. Today, it’s a policy that we can actually enforce.
Aireye’s SaaS solution requires no network or architectural changes...
Medical devices are life-critical - Aireye ensures no unauthorized connections to Hadassah’s devices and prevents…. this was just a policy on paper. Today, it’s a policy that we can actually enforce. 
 Aireye eliminated a multitude of blind spots for me, including unseen devices… It prevented unwanted unsecured network connection attempts from our portable medical device machine and helped detect unseen Wi-Fi radios in our workstations.
Aireye eliminated a multitude of blind spots for me, including unseen devices… It prevented unwanted unsecured network connection attempts from our portable medical device machine and helped detect unseen Wi-Fi radios in our workstations. 
We Safeguard Our Customers’ Critical Assets

Protect your devices from being hijacked and manipulated

Prevent devices from being rendered unusable

Protect sensitive data from being leaked from devices

Protect devices from becoming a bot to attack your networks and that of others

Monitor consumer devices (smart speakers, TVs) for eavesdropping, etc. (leaking sensitive data)
Trusted by Healthcare, Defense & Other Industries











Recognized in Market Guides and Emerging Tech
| 2024 Market Guide for Medical Device Risk Management Platforms
| 2024 Emerging Tech: Top Security Concerns for Cyber Electronic Defense
| 2024 Emerging Tech: Security — The Need for Wireless Airspace Defense
| 2023 Market Guide for CPS Protection Platforms
| 2023 Market Guide for Medical Device Security Solutions
| 2022 Gartner® Cool Vendor in Hybrid Work Security
| 2022 Market Guide for Medical Device Security Solutions
| 2022 Market Guide for Operational Technology Security
| 2022 Emerging Tech Impact Radar: Security
| 2022 Emerging Tech Impact Radar: Communications