If you’re dealing with the security of your corporation, you should be concerned about the recently released Fragattacks. Coupling FragAttacks with Antenna for Hire means that the attacks can be carried out remotely. The combination of both makes them a perfect storm in the corporate network airspace, while leaving no attack traces in the network logs.
FragAttacks Overview
The FragAttacks (short for Fragmentation and Aggregation Attacks) class is a subset of digital airborne attacks performed over Wi-Fi, discovered by security researcher Mathy Vanhoef. The radio frames that carry the communication data are deconstructed and re-assembled in a different manner that enables attackers to intercept encrypted traffic and inject their own malicious code.
FragAttacks leverage a dozen Wi-Fi vulnerabilities, either exploited separately or in conjunction with each other. Three of the vulnerabilities are design flaws and the rest are implementation flaws. The vulnerabilities affect all security versions of Wi-Fi including the latest release, WPA3. Some of the design flaws date back to 1997 to the original Wi-Fi security protocol, WEP.
6 Reasons Why FragAttacks Pose High Security Risk to Corporations
While many of the vulnerabilities are rated as MEDIUM, if you’re dealing with security within your corporation, FragAttacks pose HIGH risk to your organization:
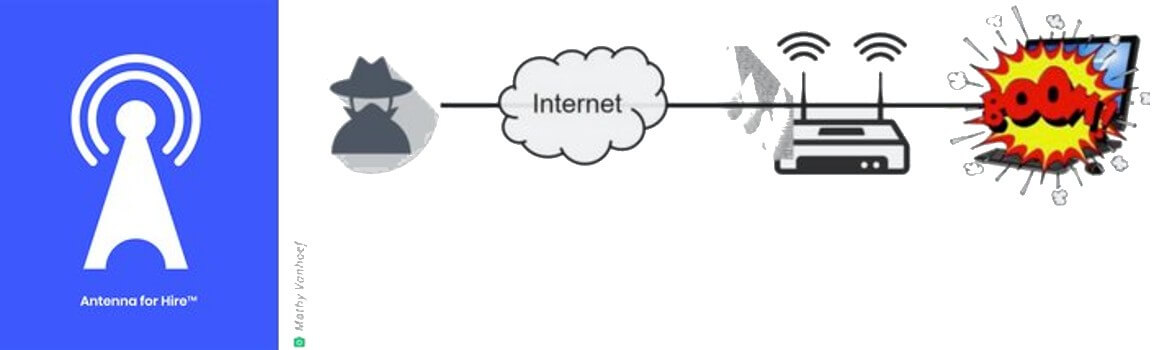
- FragAttacks can be exploited remotely. One of the biggest misconceptions of FragAttacks is that they pose a medium risk to the corporation since the attacker needs to be in physical proximity to the corporate network. However, long gone are the days of the “parking lot attack”. Given the large number of Wi-Fi capable devices deployed everywhere – inside and outside of the corporate control – an attacker can exploit any insecure device and turn it into an Antenna for Hire. Using readily available, software based, Wi-Fi attack tools, the attacker can remotely exploit FragAttacks against any network using the Antenna for Hire as a stepping stone.
- FragAttacks bypass existing network security controls such as firewalls, NAC and wireless encryption. Some of the vulnerabilities enable an attacker to directly communicate with a device behind the firewall even if that device is connected to a wired network. The reason is that an attacker can inject small IP packets within the communication that severely affect devices on the network, for example by messing up with DNS configuration.
- FragAttacks affect all wireless devices on your network. The number of vulnerabilities and their nature suggest that with high probability all devices are vulnerable.
- You can’t patch all devices. The number of vulnerable devices and the diversity of device types means that patching is not a viable solution. It is difficult enough to deploy a patch over large populations when the devices are of the same type, and the patch is easily available from the vendor. When you have so many types of devices from so many different vendors – and some of them don’t even have patches – things are beyond messy.
- FragAttacks leave no traces in your network logs. The saying “what you don’t know can’t harm you” does not hold true with cybersecurity incidents. Security talks a lot about “reducing the dwell time” and “unveiling attackers as fast as possible”. Existing security tools do not have any record of 802.11 traffic, under the assumption that anything of forensics interest must be on the IP level and above.
- FragAttacks are not a black swan, they are the tip of the iceberg. When the first chip-architecture related vulnerabilities, Meltdown and Spectre, were reported in early 2018 they were considered by part of the industry as one-offs. However, since then many such vulnerabilities were discovered and reported. The fact that some of the FragAttacks vulnerabilities have been resting around since 1997 suggests that no one was looking for them! With Mathy Vanhoef shining a spotlight on the security of Wi-Fi standards, other researchers (as well as hackers) are sure to follow with more vulnerabilities that expose the risk of digital airborne attacks.
Detecting and Preventing Fragattacks
Digital airborne attacks, including the FragAttacks, operate on a separate network dimension – the corporate’s network airspace.
Network Airspace Control and Protection (NACP) comes precisely to provide security over this increasingly exposed attack surface. NACP is an overarching solution which protects against all digital airborne attacks, removing the need to pinpoint attacks, patch point solutions and create complex semi-effective combos of tech workarounds.
AirEye vs FragAttacks
AirEye is the first and only NACP solution that prevents FragAttacks.
Exploiting the FragAttacks vulnerabilities allows the attacker to manipulate some of the Wi-Fi frames in many different ways. However, the key to this manipulation is the ability to intercept, subvert and forward traffic between a station and an AP of the victim network. This ability relies on a technique called Multi Channel Machine in the Middle (aka Evil Twin) – establishing a rogue access point carrying the exact same characteristics (SSID and BSSID) of the original access point on a different channel.
AirEye Dome detects Evil Twin devices using various techniques of monitoring and analyzing the entire Wi-Fi spectrum. AirEye Dome alerts on the existence of such a rogue device and detects any victim station attempting to communicate through it. At that point, AirEye Dome proactively prevents those communications.
For more details, contact us at [email protected]
List of FragAttack CVEs