Critical Cisco Wireless LAN Controllers exploit details go public

Published: June 3, 2025 Summary: A serious vulnerability (CVE‑2025‑20188, CVSS 10.0) has been published publicly, affecting Cisco Wireless LAN Controllers (WLCs) running IOS XE. Attackers can exploit a hard‑coded JWT secret to bypass authentication, allowing arbitrary file uploads and potential remote code execution. All Cisco customers using the affected WLC platforms should immediately apply the […]
Threat Modeling the Wireless Airspace in 2025

“Any Wi-Fi Attack Can Now Be a Remote Attack” By the AirEye Research TeamInspired by Mathy Vanhoef’s insights 1. Objective Wireless threats are no longer bound to physical proximity. Pre-auth vulnerabilities, beacon spoofing, and rogue access points can now be exploited remotely — even globally — thanks to cloud relays, malicious proxies, and antenna-for-hire models. […]
New Vulnerability Allows for Next Generation Rogue Access Point

By Uriya Elkayam – As part of our research, we found a vulnerability by-design in the Wi-Fi protocol that under OWE mode exposes Hidden Networks. This means that a hidden wireless network name is open to all, not just to a device attempting to access a pre-known hidden network.
Wi-Fi Spoofing: Employing RLO to SSID Stripping

A few months ago we published the details of a wireless vulnerability, dubbed SSID Stripping, that allows attackers to spoof Wi-Fi networks in a
Trends in Wi-Fi Vulnerabilities: This Time, It’s Qualcomm
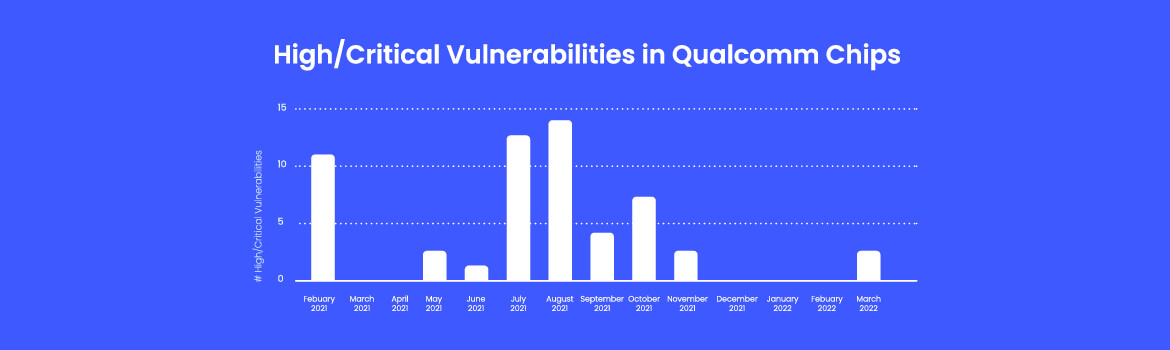
Qualcomm’s monthly security bulletins show an interesting trend with their Wi-Fi chips, which for some reason hardly receive any attention.
The Intel Vulnerabilities Disclosure: They Actually Can be Remotely Exploitable
Late last week, Intel issued security advisories, INTEL-SA-00539, INTEL-SA-00581, INTEL-SA-00582
