A few months ago we published the details of a wireless vulnerability, dubbed SSID Stripping, that allows attackers to spoof Wi-Fi networks in a very effective manner. SSID Stripping employs various techniques and recently we found an additional technique which employed RLO.
The essence of it is the use of a special Unicode character called RLO (U+202E) which reverses the display of the following characters. Hence a network with the name Corporate[RLO]krowteN is displayed identical to CorporateNetwork (see sample screenshot).
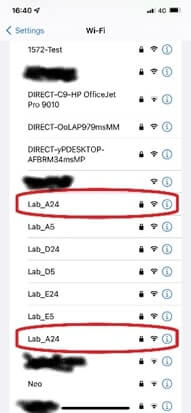
AirEye’s research team verified that this technique:
- Affects all major operating systems including Windows, Android and iOS
- Goes undetected by most solutions that attempt to identify spoofed Wi-Fi networks
RLO: an in-the-wild attack technique
RLO is a known technique in cyber-security. It was commonly used 20 years ago by attackers, but also recently, researchers found this technique exploited in the wild, in more than 400 attacks, to phish Microsoft 365 users.
This is once again a reminder that the same techniques that are already being used in many attack domains such as email phishing and file-related attacks can be applied to the network airspace attack surface. It’s not long when we’ll start seeing such mass attacks.
An Issue for Organizations
While for other domains organizations already have robust and mature security tools in place, unfortunately most organizations are not even paying any attention today to their network airspace domain. Yet, with 80% of organizational networks going through wireless, this is the largest increasing attack surface.
Test Your Organization’s Resilience to SSID Stripping
At AirEye we built a free tool that tests how vulnerable your systems are to Wi-Fi spoofing attacks such as SSID Stripping.
Download now this free tool: https://aireye.tech/hide-n-seek

