New Vulnerability Allows for Next Generation Rogue Access Point

By Uriya Elkayam – As part of our research, we found a vulnerability by-design in the Wi-Fi protocol that under OWE mode exposes Hidden Networks. This means that a hidden wireless network name is open to all, not just to a device attempting to access a pre-known hidden network.
Wi-Fi Spoofing: Employing RLO to SSID Stripping

A few months ago we published the details of a wireless vulnerability, dubbed SSID Stripping, that allows attackers to spoof Wi-Fi networks in a
Trends in Wi-Fi Vulnerabilities: This Time, It’s Qualcomm
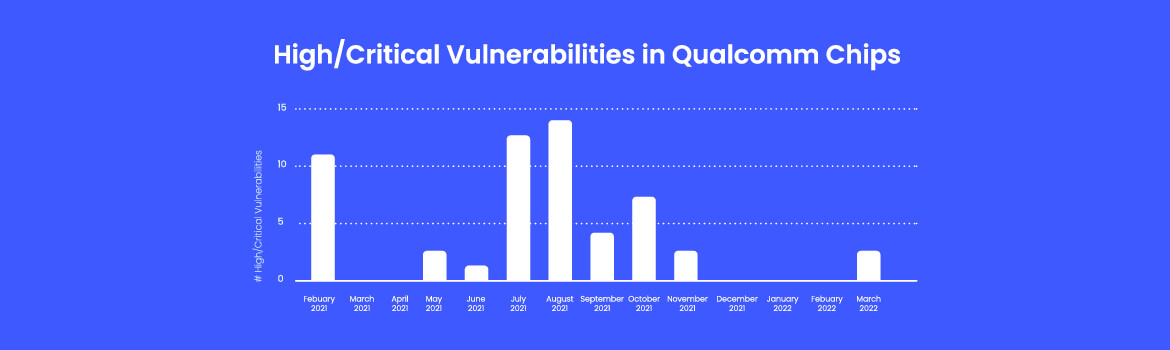
Qualcomm’s monthly security bulletins show an interesting trend with their Wi-Fi chips, which for some reason hardly receive any attention.
The Intel Vulnerabilities Disclosure: They Actually Can be Remotely Exploitable
Late last week, Intel issued security advisories, INTEL-SA-00539, INTEL-SA-00581, INTEL-SA-00582
