Does Micro-Segmentation Really Offer Ultimate Protection for OT/IoT/IoMT Devices?

Micro-segmentation – dividing up your network and setting controls for each part – is currently the trendy solution to have for securing OT, IoT, and IoMT devices, but this belief overlooks several critical realities. Limited Visibility Problem: In environments with OT, IoT, and IoMT devices, installing agents is not feasible, nor do these devices always […]
New Vulnerability Allows for Next Generation Rogue Access Point

By Uriya Elkayam – As part of our research, we found a vulnerability by-design in the Wi-Fi protocol that under OWE mode exposes Hidden Networks. This means that a hidden wireless network name is open to all, not just to a device attempting to access a pre-known hidden network.
Wi-Fi Spoofing: Employing RLO to SSID Stripping

A few months ago we published the details of a wireless vulnerability, dubbed SSID Stripping, that allows attackers to spoof Wi-Fi networks in a
Trends in Wi-Fi Vulnerabilities: This Time, It’s Qualcomm
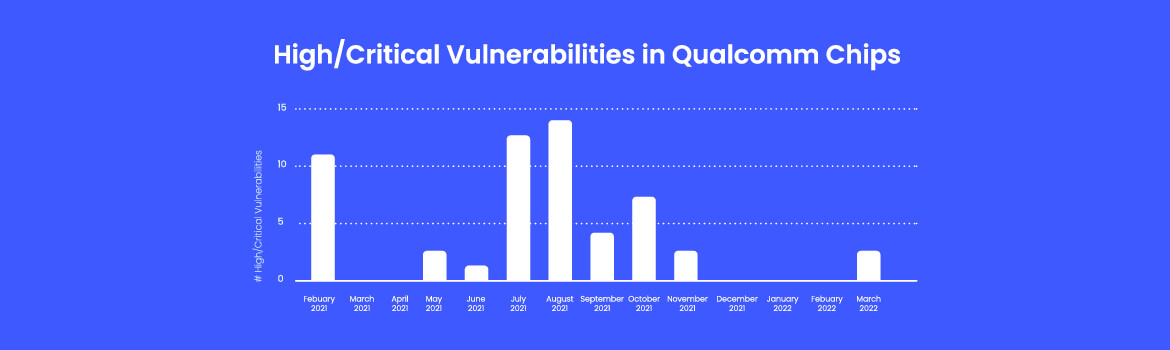
Qualcomm’s monthly security bulletins show an interesting trend with their Wi-Fi chips, which for some reason hardly receive any attention.
It’s Not About Printer Security. It’s a Hole in Your Network Security
Researchers of F-Secure recently released the details of two critical Remote Code Execution (RCE) vulnerabilities (CVE-2021-39238 and CVE-2021-39237) affecting 150 types of HP printers
The SSID Stripping Vulnerability: When You Don’t See What You Get

AirEye’s research team in collaboration with the Computer Science faculty at the Technion – Israel Institute of Technology have found…
