Tag Archives: vulnerability
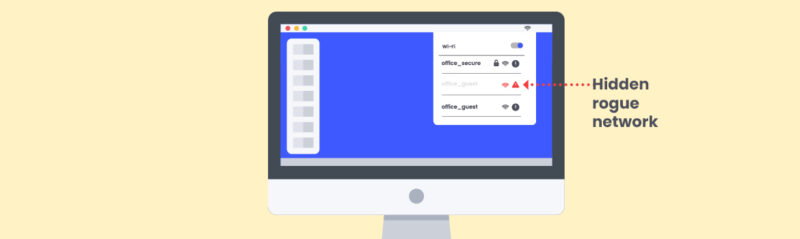
New Vulnerability Allows for Next Generation Rogue Access Point
By Uriya Elkayam - As part of our research, we found a vulnerability by-design in...
23
Feb
Feb
Wi-Fi Spoofing: Employing RLO to SSID Stripping
A few months ago we published the details of a wireless vulnerability, dubbed SSID Stripping,...
04
Apr
Apr
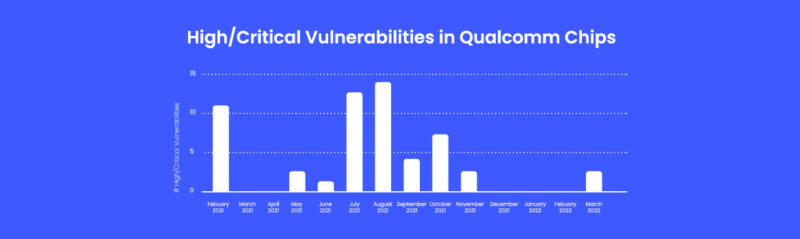
Trends in Wi-Fi Vulnerabilities: This Time, It’s Qualcomm
Qualcomm’s monthly security bulletins show an interesting trend with their Wi-Fi chips, which for some...
29
Mar
Mar
It’s Not About Printer Security. It’s a Hole in Your Network Security
Researchers of F-Secure recently released the details of two critical Remote Code Execution (RCE) vulnerabilities...
06
Dec
Dec
The SSID Stripping Vulnerability: When You Don’t See What You Get
AirEye’s research team in collaboration with the Computer Science faculty at the Technion – Israel...
13
Sep
Sep