Wi-Fi Attacks: From White Vans, to Drones and on to Antenna for Hire
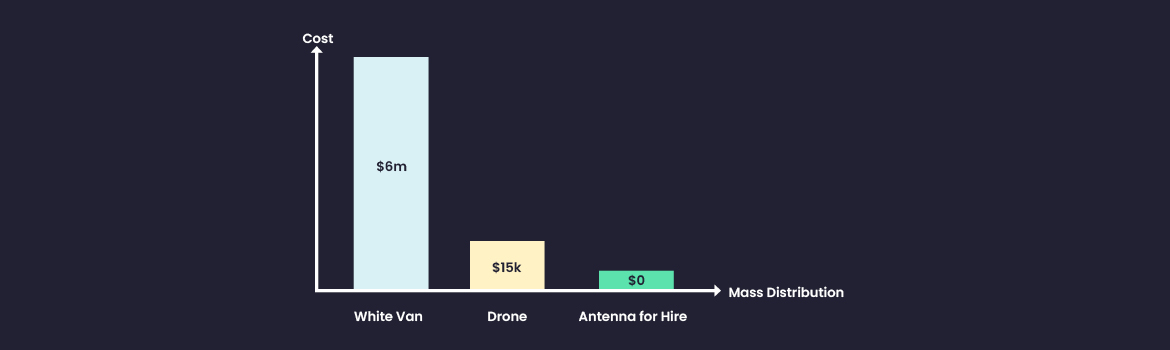
Earlier this week Greg Linares published research on a real-life Wi-Fi cyberattack against an east coast based private equity firm. The origin of the attack was a drone

Earlier this week Greg Linares published research on a real-life Wi-Fi cyberattack against an east coast based private equity firm. The origin of the attack was a drone