Earlier this week Greg Linares published research on a real-life Wi-Fi cyberattack against an east coast based private equity firm. The origin of the attack was a drone that connected to the firm’s networks over Wi-Fi. The creativity of such an attack, the fact that it actually occurred, together with the relatively low cost of it, made this news significant.
But this is just the beginning of the Wi-Fi attack trends.
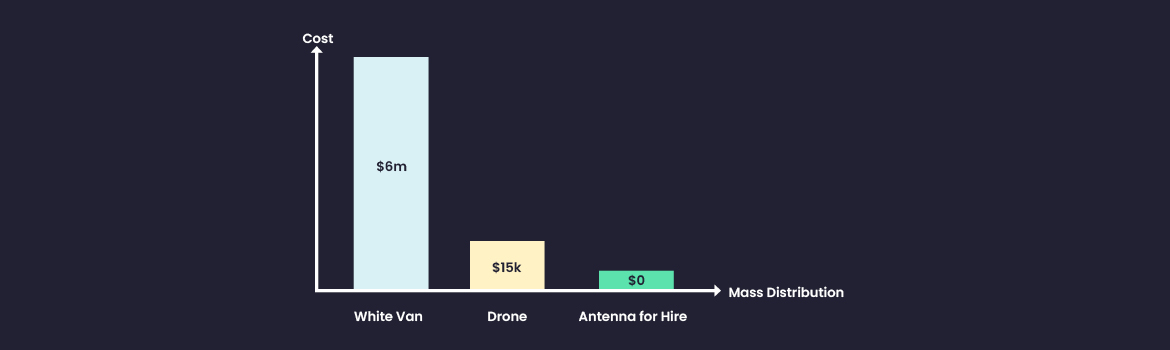
Conspicuous White Vans for Nation States
Adversaries connecting to their target Wi-Fi networks is not new. You may all recall those white vans as shown in films trying to penetrate the corporate networks by capturing over the air signals such as Wi-Fi. In fact, those white vans are still in use, even penetrating to commercial use for those who have the money to spend. Super techie, super advanced, with loads of capabilities. Their price typically range between $3.5M-$7M, as details in Forbes’ extensive research awhile back – https://www.forbes.com/sites/thomasbrewster/2019/08/05/a-multimillionaire-surveillance-dealer-steps-out-of-the-shadows-and-his-9-million-whatsapp-hacking-van/?sh=50c3197f31b7
Wi-Fi Drones for Commercial Attackers
The drone Wi-Fi attack showed that the cost of a Wi-Fi attack can easily be reduced to just $15K.
The drone attack is not new as well. BlackHat EU 2016 already presented a similar research tool – https://www.blackhat.com/docs/eu-16/materials/arsenal/eu-16-CROZONO-Framework-Leveraging-Autonomous-Devices-as-an-Attack-Vector-on-Indutrial-Networks.pdf. However, the fact that this type of attack actually occurred and its accessibility means that commercial attacks have now adopted Wi-Fi attack tools to their arsenal.
Although the price tag moves Wi-Fi attacks to commercial hackers, it still holds a big cost beyond the financial figures. First, the drone requires an operator in the target’s proximity. Second, the attackers take the chance that the drone will be exposed, making their attack a one-off attempt.
Needless to say, commercial attackers have a target set in mind to perform a Wi-Fi drone attack.
Antenna for Hire for Everyone
Looking at Wi-Fi cyberattacks today, their cost has been reduced to just above 0$.
Take this scenario:
- A remote attacker searches for a vulnerable Wi-Fi capable device on Shodan.io.
- Having gained root privilege, the attacker scans for Wi-Fi networks in its airspace. These can be Access Points, or Wi-Fi peer to peer connections on IoT devices – checking against ExploitDB that they are exploitable.
- The attacker uses one of many Wi-Fi free attacking tools (such as “Airgeddon”, “Wifiphisher” etc.) to force a connection to the targeted network.
- Once the Wi-Fi enabled device is connected to the corporate network, the attacker now assumes a foothold in the corporate network.
It’s intuitive to now call that device in the IoT botnet, or any wireless-enable device broadcasting into the corporate network, an Antenna for Hire.
An Antenna for Hire can be the router of the nearby cafe, the neighbor’s CCTV camera or boardroom monitor, a passerby’s laptop hotspot, etc.
Then consider the wireless-enabled device that belongs to the corporate, to be called a Wireless Receptor.
A Wireless Receptor can be an employee’s laptop with hotspot enabled, a lab’s access point, a Wi-Fi enabled printer, a boardroom monitor, and devices that generate their own wireless networks such as an MRIs or a forklift.
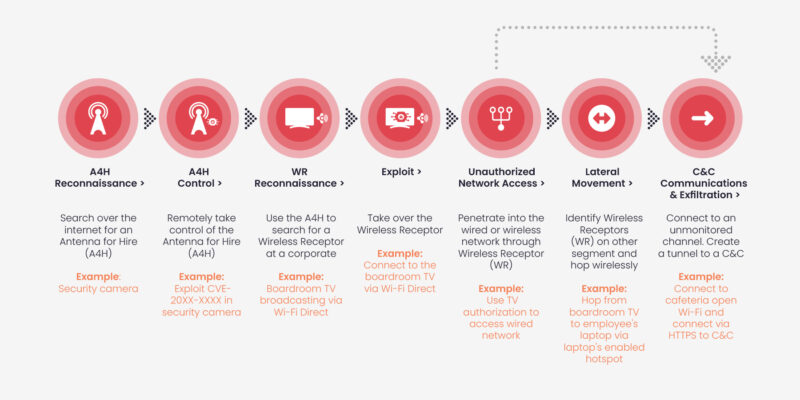
Over the air attacks that leverage Antenna for Hire are cheap, they happen remotely and are stealthy. Physically unseen, and undetected by other cybersecurity tools, attackers can reuse them over and over again.
The Trend of Over the Air Attacks
The increase of Wi-Fi enabled devices – both Wireless Receptors and Antenna for Hire, and consequently their density, makes over the air attacks accessible and easier to carry out.
The trend of over the air attacks has already started:
- Malware such as Emotet, Netwalker and Mirage had Wi-Fi propagating capabilities.
- A survey between Incident Responders (IR) showed that 44% of the experienced IR professionals had investigated at least one Wi-Fi related attack.
- We’re seeing an increase in attacks such as an employee’s laptop’s wireless traffic being redirected to the neighboring office’s CCTV camera.
- Not long ago, Hedgehog security, a UK-based Incident Response (IR) company sent us a report technically detailing an over the air attack at an institution where 94GB of data was exfiltrated over Wi-Fi hotspots. The full report can be found here:
https://aireye.tech/resources/hedgehog-ota-attack-lp/
Time and again we’ve seen how commercial attack tools integrated nation states capabilities. We see the trend in the cost of carrying out the attacks. We’re bound to see this too in the sophistication of over the air attack tools.
The network airspace is your largest increasing attack surface. It’s time to start looking after it.