Introduction
How should your network security stack look like? Here we show how attackers bypass current security solutions through the network airspace, such as the latest Wi-Fi drone attack, and how the network security stack should be updated accordingly.
The Typical Corporate Network Security Architecture Model
As a start, let’s take a look at the current and typical corporate network security (wired, wireless or even virtual such as SASE) architectural model:
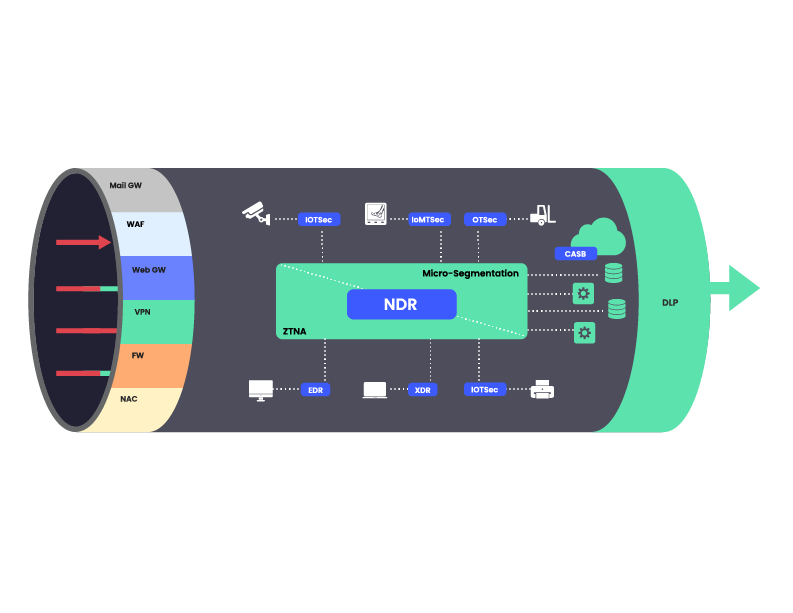 Figure 1: A high level architectural view of corporate network security
Figure 1: A high level architectural view of corporate network securityPreventive Solutions at the Entry Points
At the entry points, preventive security solutions are stacked to enforce that only legitimate traffic enters the network. The purpose of these solutions is to prevent initial compromise of servers and devices on the network and prevent traffic from unknown sources to reach corporate devices.
Preventive Solutions at the Exit Points
At the exit points, Data Leakage Prevention (DLP) solutions are placed to ensure that only policy-allowed data leaves the corporate.
Detection Within the Network
While the above solutions serve as an initial gatekeeper, additional security solutions are deployed for when an attacker has already established a foothold within the organization.
When Wireless Capabilities are Added
The wireless capabilities of the devices on the network changes the above illustration. These open up a new attack surface as well as internal network paths that are uncovered by existing security solutions.
While wireless capable devices are connected securely to the corporate network (whether wired or wireless), they are inherently open to accepting and processing network traffic transmitted by any other device in their proximity. They are also capable of sending out insecure network traffic.
Wireless Receptors
In essence, today’s corporate network is perforated with gaps generated by these corporate-owned dual-connected devices, aka Wireless Receptors.
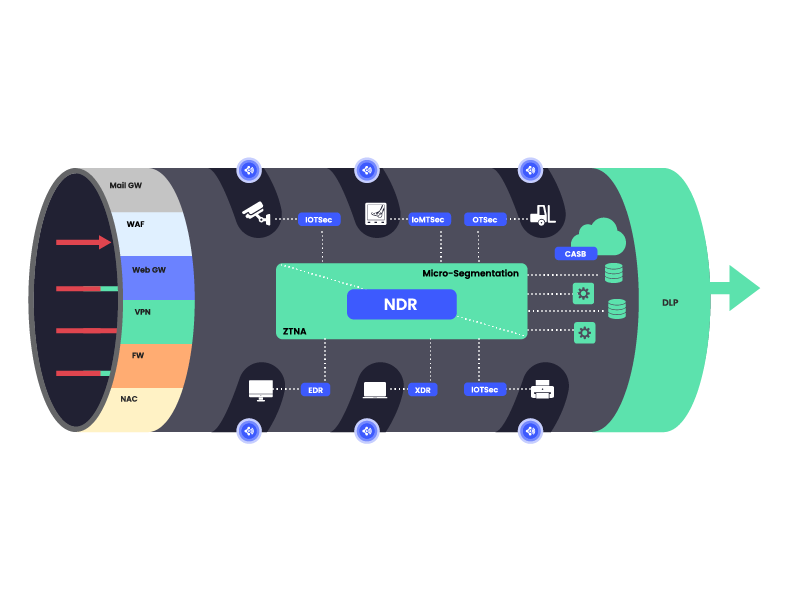 Figure 2: Wireless Receptors create leakage from the corporate network
Figure 2: Wireless Receptors create leakage from the corporate networkThese Wireless Receptors create new and uncontrolled entry and exit points into and out of the corporate network.
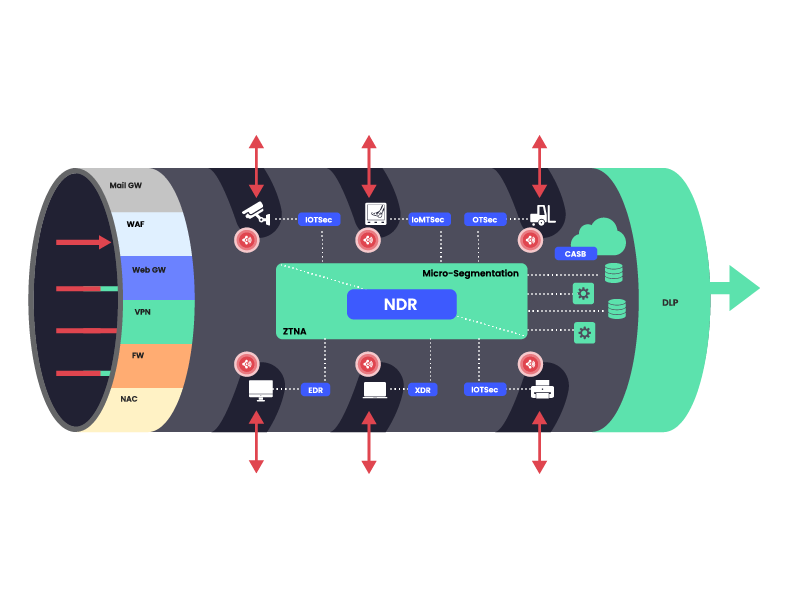 Figure 3: Wireless Receptors become uncontrolled entry and exit points
Figure 3: Wireless Receptors become uncontrolled entry and exit pointsWireless Receptors also create internal insecure network paths. These internal networks, called Shadow Networks, additionally defeat micro-segmentation solutions.
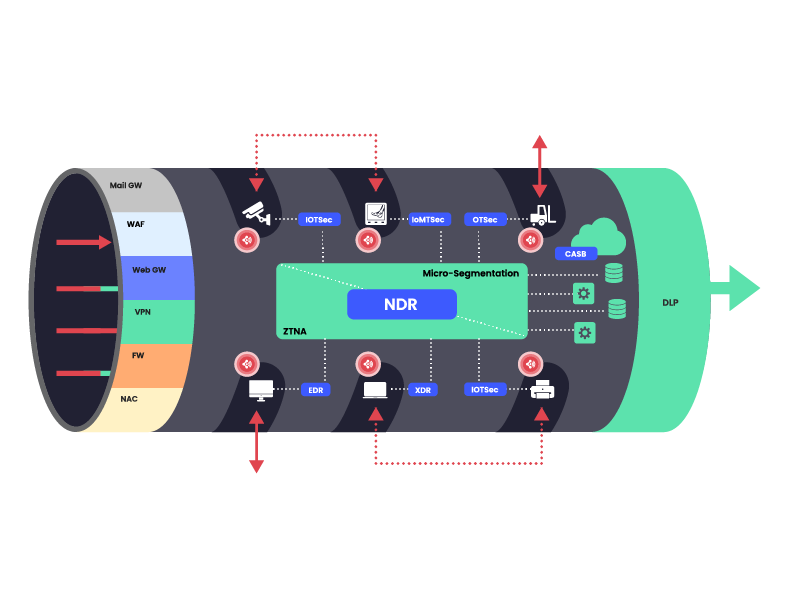 Figure 4:Wireless Receptors defeat micro-segmentation efforts
Figure 4:Wireless Receptors defeat micro-segmentation effortsAntenna for Hire
The corporate network is surrounded by an infinite number of Antenna for Hire. These are wireless devices that broadcast in the corporate network. These can be laptops, open-source Access Points (openWRT), the wireless router in a neighboring cafe, personal mobile phones, OT and IoT devices such as Wifi cameras, TVs, monitors, A/C units, etc.
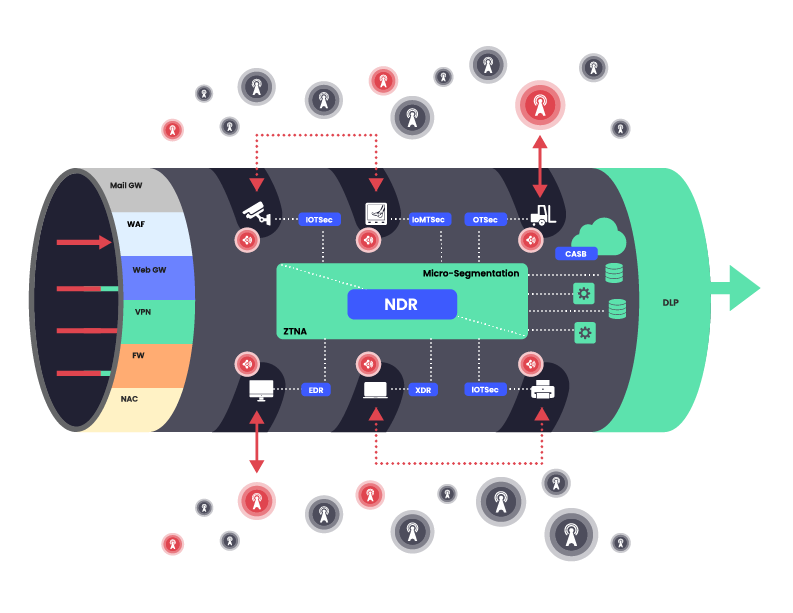 Figure 5: Antenna for Hire that are operated remotely and through software-only interact with Wireless Receptors
Figure 5: Antenna for Hire that are operated remotely and through software-only interact with Wireless Receptors Today’s attack tools can compromise an Antenna for Hire remotely and through software-based tools. From there the attacker can connect wirelessly to the Wireless Receptor and penetrate the network or act as an exfiltration destination.
NACP: Controlling and Protecting the Network Airspace
Network Airspace Control and Protection (NACP) is an additional network security layer that closes these wireless holes. The NACP prevents the wireless-led attack from entering and exiting the corporate network as well as extends network and micro segmentation by preventing wireless lateral movement.
NACP can easily be defined as the dynamic enforcement of wireless security policies based on an understanding of communicating wireless devices and their interactions.
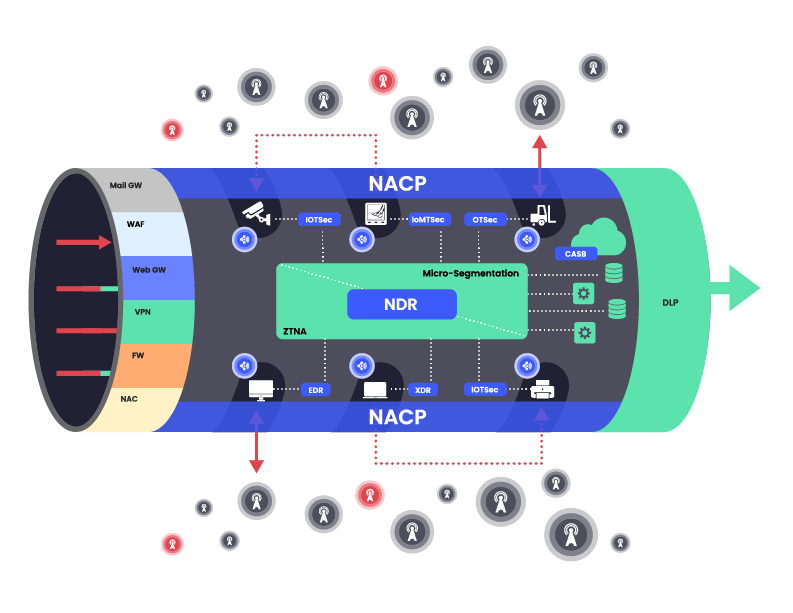 Figure 6: How NACP fits into network security architecture
Figure 6: How NACP fits into network security architecture
